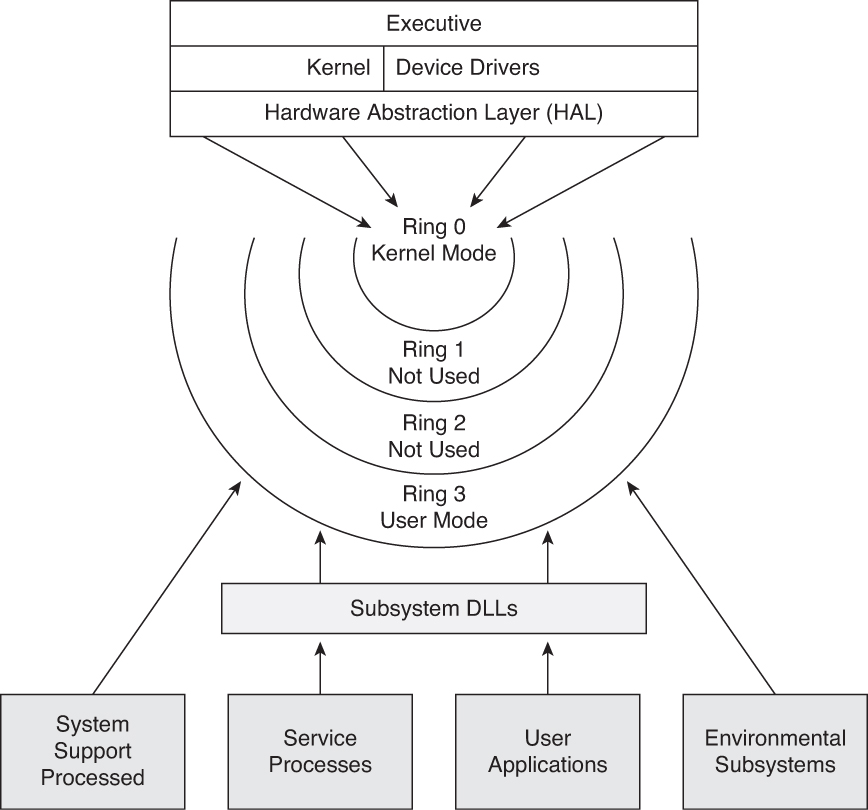
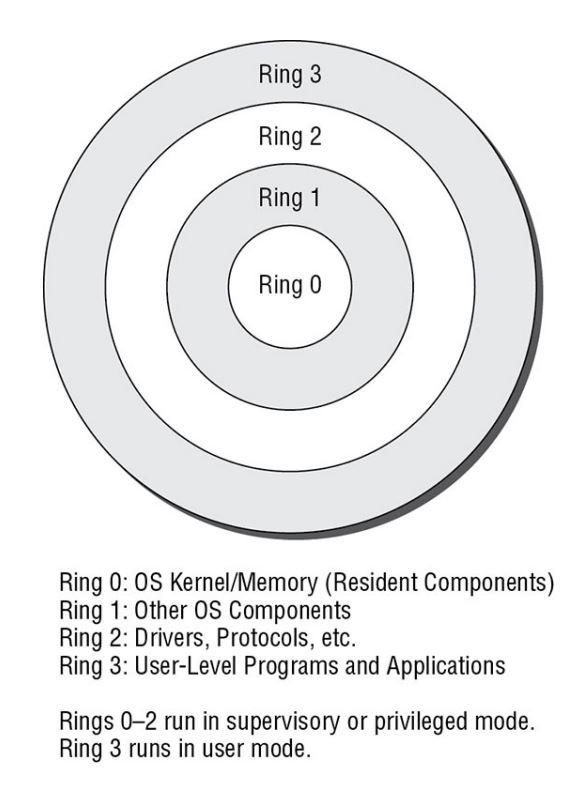
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification
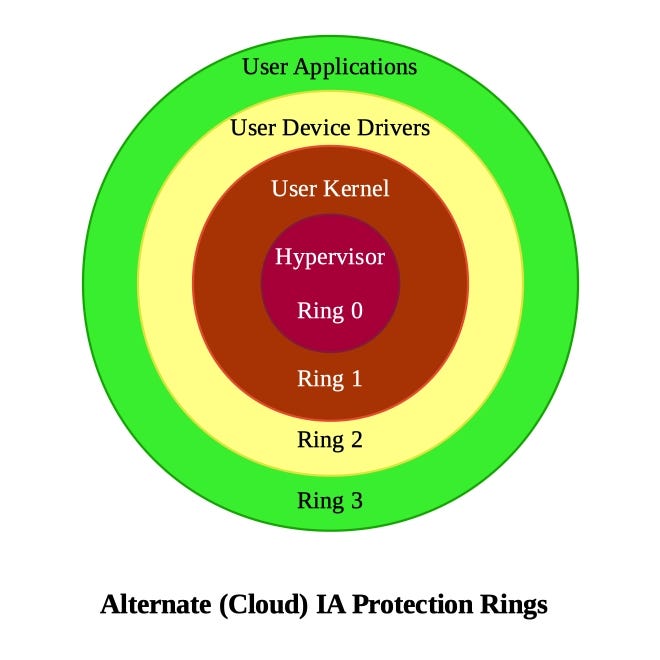
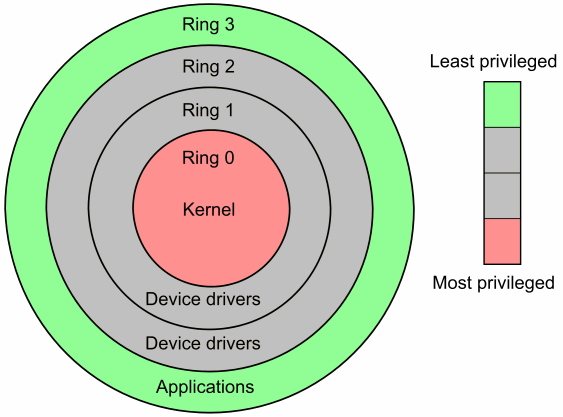
Operating system privilege rings in most modern hardware platforms and... | Download Scientific Diagram
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium
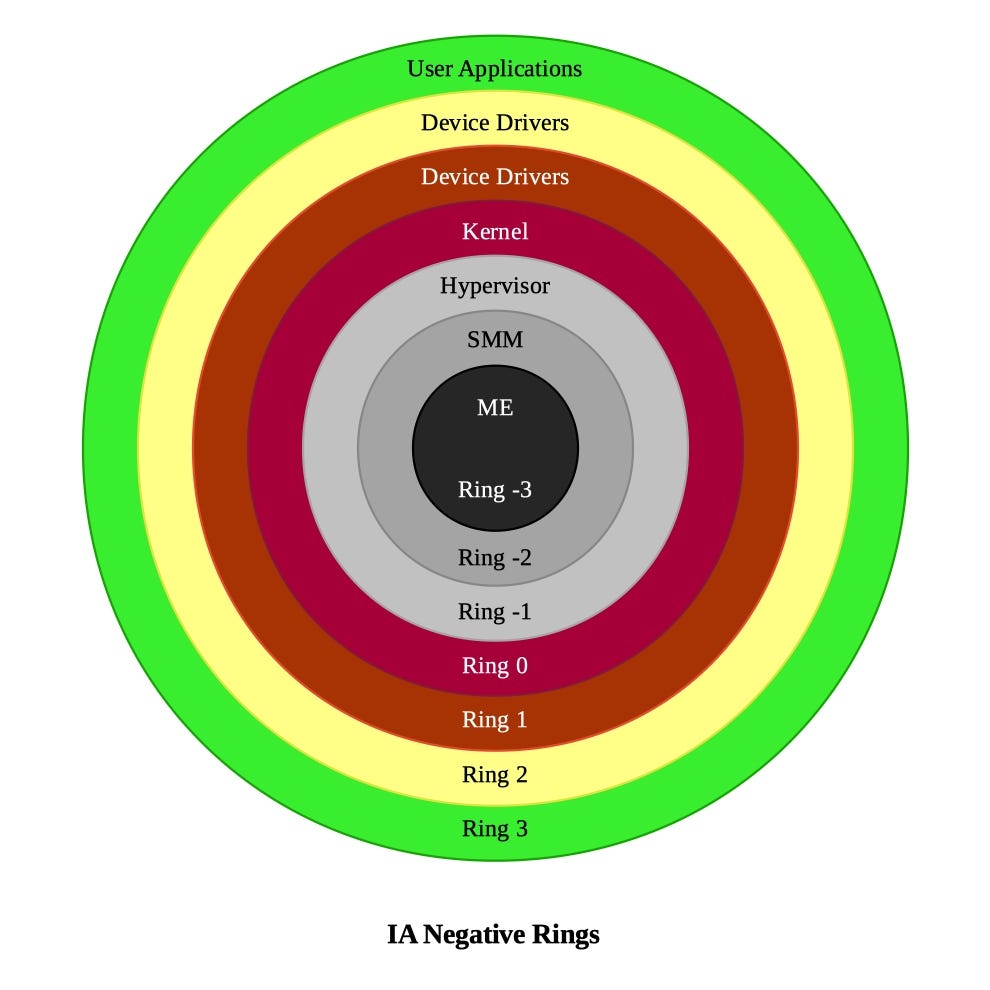
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium

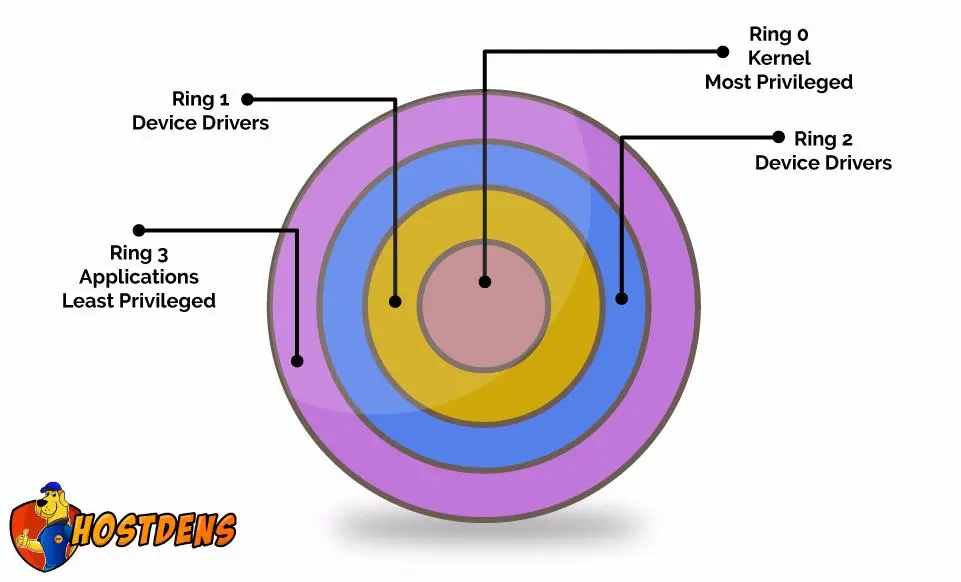
What is kernel rings in a system ? | kernel protection ring | cloudpradeep | by cloud pradeep | Medium

![Intel's Ring Architecture [28, 37, 24, 14] | Download Scientific Diagram Intel's Ring Architecture [28, 37, 24, 14] | Download Scientific Diagram](https://www.researchgate.net/publication/50875025/figure/fig2/AS:671525288038404@1537115513180/Intels-Ring-Architecture-28-37-24-14.png)
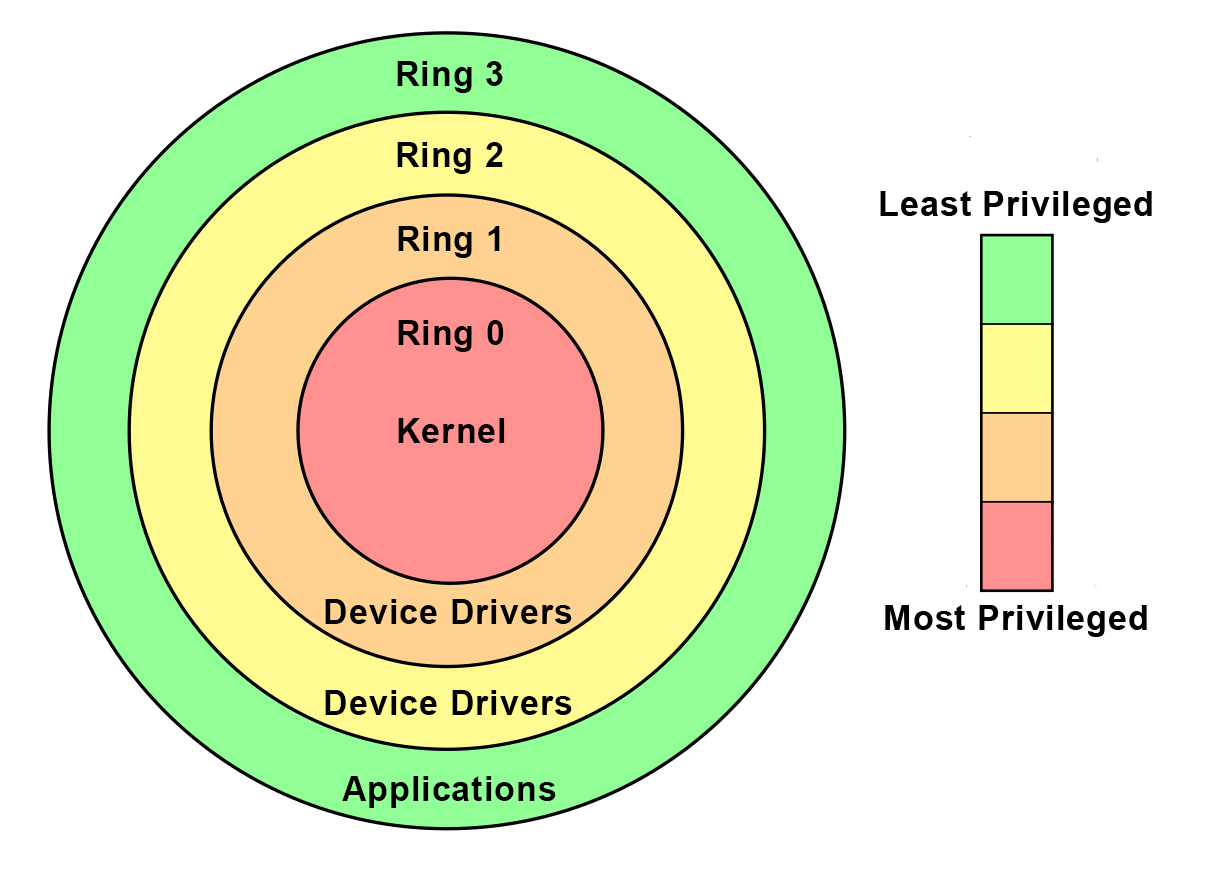

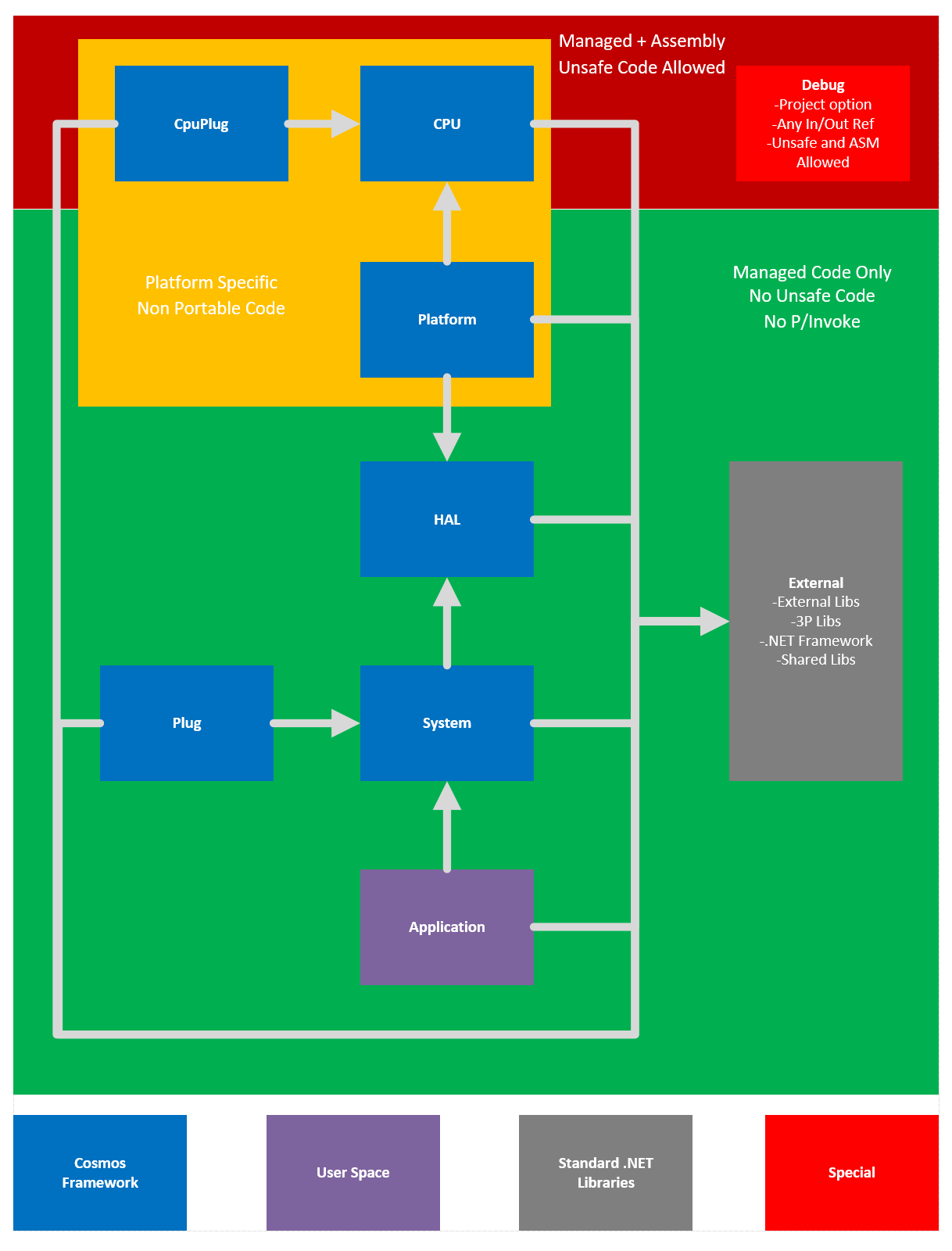
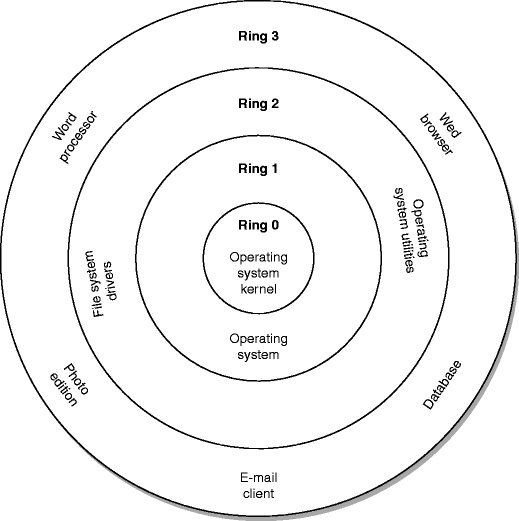









![UserLand versus kernel land - Advanced Infrastructure Penetration Testing [Book] UserLand versus kernel land - Advanced Infrastructure Penetration Testing [Book]](https://www.oreilly.com/api/v2/epubs/9781788624480/files/assets/71f40671-14f8-409f-8bba-d60164553c8e.png)